Performance Measures
01.08.2013
Budget, fusion center, homeland security intelligence, Information sharing, intelligence, intelligence center, Performance Measures, Strategy, Uncategorized
 The Department of Homeland Security (DHS) released its 2012 National Network of Fusion Centers Assessment Report and the results are encouraging. DHS reported that (overall) fusion centers improved their capability scores by 11 points over the 2011 assessment report card. Summary findings, based on Critical Operating Capabilities (COCs):
The Department of Homeland Security (DHS) released its 2012 National Network of Fusion Centers Assessment Report and the results are encouraging. DHS reported that (overall) fusion centers improved their capability scores by 11 points over the 2011 assessment report card. Summary findings, based on Critical Operating Capabilities (COCs):
COC 1 – Receive
- All fusion centers (77 or 100%) have access to federally sponsored Sensitive But Unclassified (SBU) information sharing systems.
- Every fusion center (77 or 100%) has at least one person cleared to access Secret information, but regular staff turnover means that fusion centers will continue to request new clearances (approximately 500 new clearance requests in the next 12 months).
- A significant number of fusion centers have on-site access to classified information sharing systems (66 or 85.7%).
- Fusion center use of the DHS Secret Internet Protocol Router Network (SIPRNet) Whitelist (Whitelist) is limited (41 or 53.2%).
COC2 – Analyze
- Fusion centers are highly involved in assessing threat and risk for their area of responsibility (AOR) (72 or 93.5%).
- Fusion centers are obtaining and using customer feedback on their analytic products (structured feedback: 65 or 84.4%).
- Analytic production plans are used widely across the National Network (60 or 77.9%).
- Critical infrastructure protection capabilities continue to expand across the National Network (75 or 97.4%).
COC 3 – Disseminate
- Despite progress since 2011, less than half (35 or 45.5%) of the National Network have a process in place to verify that customers are receiving their products.
- Fusion centers are increasingly designating a single, primary information sharing system (72 or 93.5%), but Homeland Security Information Network (HSIN) Intel is not frequently cited (23 or 29.9%) as the primary system for unclassified communication between fusion centers.
COC 4 – Gather
- The number of fusion centers that have developed Standing Information Needs (SINs) has increased (59 or 76.6%), but continued attention to SINs development is necessary.
- The National Network has a robust request for information (RFI) management capability (69 or 89.6%).
- A significant percentage of the National Network are involved in the Nationwide Suspicious Activity Reporting (SAR) Initiative (NSI), in particular in providing line officers with information on the behaviors identified in the Information Sharing Environment (ISE)-SAR Functional Standard (SAR line officer training: 66 or 85.7%).
DHS has identified three areas for improving fision center capabilities:
- Use Standing Information Needs (SINs) as the foundation of a customer-driven fusion process:
Fusion centers need to have a process for a) deriving and cataloguing regional and federal information and intelligence needs SINs , and b) actively tagging/associating these SINs with the information and intelligence products they produce.
- Document key business processes and ensure consistent access to training:
High turnover in critical fusion center staff positions is going to be the norm, for a number of reasons – staff rotations, augmentation, contract renewals, promotions, etc. Fusion Center Directors must plan for this “churn” by taking the time to a) document the center’s core business processes, b) keep SOPs and policies up to date, and c) develop training and other performance support tools to minimize the impact of staff turnover on center operations.
- Implement organizational planning and evaluation processes to continuously improve fusion center operations:
Fusion centers should clearly develop and communicate their center’s mission, goals, and objectives by developing a strategic plan, and using that plan as a tool to measure its performance. The strategic plan and periodic performance reports should help to communicate how investments in the fusion center result in tangible results, and b) help to drive annual budget requests to sustain or enhance current center capabilities.
I see gaps in these areas in my own work with fusion centers…unfortunately, many fusion centers are so busy with operational activities, that developing SOPs, training, strategic plans, etc., ends up on the back burner.
One other area, not directly addressed by the DHS assessment process is the development of an effective plan and roadmap for building an IT infrastructure that supports the four COCs. This too gets relegated to the back burner. In some cases, IT is addressed, but in a piecemeal fashion – Fusion Center Directors should elevate the need for an integrated IT plan, one developed from Fusion Center business processes and describes three key areas.
Suggested Components of a Fusion Center IT Strategy
- Information and Intelligence exchanges – what information, data, and intelligence comes-in and goes-out of the Fusion Center?
- What functional capabilities does the Fusion Center have now and which systems deliver those capabilities? (as-is)
- What NEW functional capabilities does the Fusion Center need, and how will the center procure them? (to-be)
- How much money does the Fusion Center need to a) sustain current capabilities and b) to implement the new capabilities?
Feel free to reach out to me if your center would like to discuss enhancing your operational and/or IT planning capability.
r/Chuck
03.08.2009
data sharing, Evaluation, Information sharing, LEIS, NIEM, Performance Measures
 I just finished reading of your appointment on the FederalNews Radio website. As you begin your review of the state of information sharing and the ISE, I would like to offer up some thoughts as someone who has been an information sharing evangelist for nearly a decade. here are seven points to consider:
I just finished reading of your appointment on the FederalNews Radio website. As you begin your review of the state of information sharing and the ISE, I would like to offer up some thoughts as someone who has been an information sharing evangelist for nearly a decade. here are seven points to consider:
- Resist the urge to see information sharing as an outcome. Information sharing is a means to an end, not the end itself. Each federal agency, every state and regional fusion center, and all law enforcement intelligence units should have a clear set of information requirements, questions if you will, that information sharing and the intelligence process should work to answer–hold agencies accountable for having clear and valid requirements. This has been a common practice in the intelligence community for decades and should be a practice for all information sharing elements.
- Build clear accountability into the information sharing process. Every federal agency, fusion center and law enforcement agency should have one person, preferably an impassioned, well-respected leader, that can ensure that their agencies requirements are well documented and communicated horizontally across federal boundaries and vertically to local, state, and municipal agencies, and (where applicable) private sector organizations.
- Establish clear linkage of information sharing to agency operational performance measures. Just as staffing, information technology, facilities, and utilities are seen as strategic resources in a performance-based budget, information sharing must be seen as a resource to be strategically used to help an agency achieve its mission. When measuring the success of information sharing, focus on the extent to which it helped achieve agency goals–just as counting cases in law enforcement is a misleading way to judge public safety success, counting RFIs, records shared, SARs submitted is not a good way to gauge information sharing success–successful information sharing can only be measured through the extent to which it helps agencies (at all levels) achieve their operational goals.
- Discourage agencies from using stovepiped portals for information sharing. All shareable data should be available as a “service” for consumer agencies to ingest into their systems and not through a dedicated portal that users will need a discrete login to access. You can read my previous “Portal-mania” blog post for more detail here, but all federal agencies should be required to make their data accessible through National information Exchange Model (NIEM) based web services. This will enable consumer agencies to integrate multiple data streams into their workflow and will reduce the number of websites and portals analysts are required to access to perform their work.
- Give the same amount of attention to what is shared and how it is shared. Over the last few years, a significant amount of effort has gone into how information is shared at the expense of understanding the depth and breadth of information actually being shared. Many regional and national information sharing efforts still only contain basic levels of information, or worse are just pointer systems that require additional human effort to gain access to the actual record. Encourage agencies to communicate to each other what specific information is being shared, and what is not being shared, and help everyone understand the consequences of their decisions.
- Encourage maximum use of NIEM and the Information Exchange Package Descriptions (IEPD) contained it its clearinghouse. NIEM has emerged as the dictionary of shareable data elements. When you string together sets of these data elements to satisfy a specific business need, an IEPD is born. The NIEM IEPD clearinghouse contains more than 150 IEPDs, many of which apply to national security, law enforcement and public safety missions. While many federal agencies have pledged their support of NIEM, more effort is needed to ensure that they first seek to use IEPDs already contained in the clearinghouse and do not develop one-off IEPDs designed to meet very narrow applications.
- Finally, foster a culture of transparency to help communicate an appreciation of personal civil rights and civil liberties. All information sharing and intelligence operations should engage in proactive efforts to help alleviate any fears that individual privacy and liberties are violated by any of the actions taken by those agencies. In my September 3, 2009 blog posting I list ten questions a fusion center director should ask of their own intelligence operations. I’d like to offer up these questions as a beginning framework for any information sharing or intelligence operation. They also serve as a good framework for evaluating the extent to which information sharing and intelligence operations are in fact seriously working to do the right thing.
In closing, I hope you can see how these seven points help to frame how you might structure a results oriented evaluation of information sharing across our federal agencies and with our state and regional fusion center, and private sector partners. Taken together you will be able to report the extent to which agencies have:
- Documented their information sharing requirements – what needs to be shared;
- Someone who can be directly held accountable for effective and proper information sharing;
- Linked their need for information to specific operational goals and strategies;
- Implemented mechanisms that makes it easy for other agencies to access their information;
- Ensured that they are sharing the right information (most meaningful) information;
- Taken advantage of NIEM as a way to save money and expedite information sharing; and
- Taken measures to proactively diffuse public (and media) perceptions of information misuse.
I wish you well in your new role as Senior Director for Information Sharing Policy.
Regards,
Chuck Georgo
chuck@nowheretohide.org
02.01.2009
CJIS, data sharing, Evaluation, Information sharing, law enforcement, Law enforcement information sharing, LEIS, Performance Measures, Processes, public safety, SOA, Strategy, Technology, Uncategorized
Tom Peters liked to say “what gets measured gets done.” The Office of Management and Budget (OMB) took this advice to heart when they started the federal Performance Assessment Rating Tool (PART) (http://www.whitehouse.gov/omb/part/) to assess and improve federal program performance so that the Federal government can achieve better results. PART includes a set of criteria in the form of questions that helps an evaluator to identify a program’s strengths and weaknesses to inform funding and management decisions aimed at making the program more effective.
I think we can take a lesson from Tom and the OMB and begin using a formal framework for evaluating the level of implementation and real-world results of the many Law Enforcement Information Sharing projects around the nation. Not for any punitive purposes, but as a proactive way to ensure that the energy, resources, and political will continues long enough to see these projects achieve what their architects originally envisioned.
I would like to propose that the evaluation framework be based on six “Standards for Law Enforcement Information Sharing” that every LEIS project should strive to comply with; they include:
1. Active Executive Engagement in LEIS Governance and Decision-Making;
2. Robust Privacy and Security Policy and Active Compliance Oversight;
3. Public Safety Priorities Drive Utilization Through Full Integration into Daily Operations;
4. Access and Fusion of the Full Breadth and Depth of Regional Data (law enforcement related);
5. Wide Range of Technical Capabilities to Support Public Safety Business Processes; and
6. Stable Base of Sustainment Funding for Operational and Technical Infrastructure Support.
My next step is to develop scoring criteria for each of these standards; three to five per standard, something simple and easy for project managers and stakeholders to use as a tool to help get LEIS “done.”
I would like to what you think of these standards and if you would like to help me develop the evaluation tool itself…r/Chuck
Chuck Georgo
chuck@nowheretohide.org
www.nowheretohide.org
29.08.2007
Performance Measures, Processes, SOA, Strategy
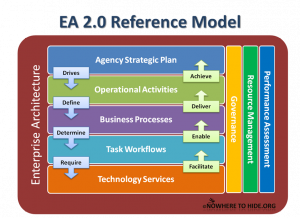
After some time thinking about my last post about EA being dead, I decided to resurrect it and marry it up with three other diciplines that I have been working in for the last 10 years; that being Strategic Management, Business Process Management and (now) Service Oriented Architecture. If you’re going to use the word “enterprise” in the context of architecture, then doesn’t it make sense to include the WHOLE enterprise?
So, the result of my thinking is shown below – I’m calling it EA v2.0. When you look at the diagram, the one thing to pay attention to is the relationships between the layers of the model, and not so much what’s in each layer. The fact is that fairly mature methodologies exist for every layer. This model is my attempt to build better understanding about the linkages BETWEEN the layers. In other words, there are a lot of models out there for conducting strategic planning, business process modeling, workflow management, and technology archtiecture; however, I have yet to find anything that explains in simple terms how all this crap ties together in a way that organization executives can understand.
So, take a look at my EA v2.0 reference model below and tell me what you think….r/Chuck
26.06.2007
Evaluation, Performance Measures
On May 31, 2007, Clay Johnson released a memorandum to the President’s Management Council to annouce the establishment of an effort to get agencies to document “Where they would be proud to be” in two years (2009). This memorandum represents OMB’s next step in its effort to get Federal agencies to “Green” in each of the five categories of the President’s Management Agenda – Strategic Management of Human Capital, Competitive Sourcing, Improved Financial Performance, Expanded eGovernment, and Performance Improvement (aka Budget and Performance Integration).
OMB is to be commended for continuing to devise creative ways to get the attention of Federal program executives focused on what is really happening in their agencies and the extent to which a) resources are effectively applied to the problems at hand, b) processes and infrastructure investments directly support delivery of meaningful services (outputs), and c) those servies do in-fact lead to meaningful results (outcomes).
In my opinion, this latest OMB strategy takes government performance accountability to the next level by making it “more personal” – Clay specifically asked each agency to indicate “where they would be proud to be on July 1, 2008 and July 1, 2009″ with respect to each of the five PMA initiatives. If successful, this initiative will engage agency executives to make a personal statement of what they would be proud to achieve in the stated timeframes. And, I am all for strategies and initiatives that put performance planning more in the hands of agency operators than in detached planning staffs.
The entire 78 page memorandum can be seen at: http://www.cio.gov/documents/PTB5_Memo_Attachments.pdf
Comments welcome…r/Chuck
 The Department of Homeland Security (DHS) released its 2012 National Network of Fusion Centers Assessment Report and the results are encouraging. DHS reported that (overall) fusion centers improved their capability scores by 11 points over the 2011 assessment report card. Summary findings, based on Critical Operating Capabilities (COCs):
The Department of Homeland Security (DHS) released its 2012 National Network of Fusion Centers Assessment Report and the results are encouraging. DHS reported that (overall) fusion centers improved their capability scores by 11 points over the 2011 assessment report card. Summary findings, based on Critical Operating Capabilities (COCs): I just finished reading of your appointment on the
I just finished reading of your appointment on the 